NEXT GENERATION ENDPOINT SECURITY
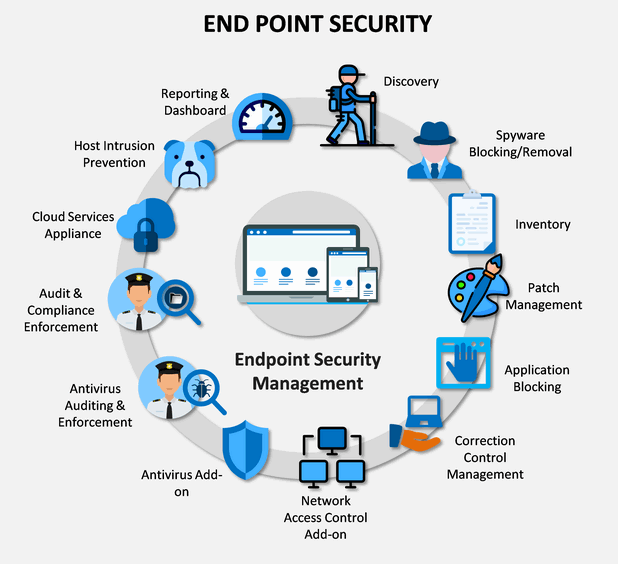
Many organizations face the need to reevaluate their approach to endpoint security – to recognize the existing gaps and have a next generation endpoint security to address the challenges of today and tomorrow.
With the latest cybersecurity attacks and breaches, it has become evident that the endpoint has become the latest battleground. Desktops and mobile devices face increasingly complex and numerous attacks by malicious software (malware) authors attempting to gain an entry point into the network to exfiltrate data or, through ransomware, for financial benefit.
Attackers are not only attacking vulnerabilities in endpoints but are exploiting features within well-known applications. Recent research from SensePost has shown that exploiting features within common Microsoft Office applications have a close to 100% success rate.
KEY BENEFITS
Peace of mind that business-critical applications are protected 24x7x365.
Removes the complexity of continuous rule-based management allowing in-house IT teams to focus on the tasks the business needs.
Increases visibility into user behavior and extends protection against email attachment and web-based attacks to reduce the risk of infection by zero-day malware.
Businesses will have endpoints fully updated malware detection mechanisms in place.
Endpoint Detection and Response
Endpoint detection and response solutions collect, record, and store large volumes of data from endpoint activities to provide security professionals with the comprehensive visibility they need to detect, investigate, and mitigate advanced cyber threats.
Traditional antivirus solutions, as well as other, more-pointed solutions, provide enterprises with preventative endpoint protection, which means they react to new files entering a system and, if deemed malicious, automatically stop them from running. Despite this, attackers are still able to penetrate endpoints. This is because they use innovative techniques that stealthily compromise systems without triggering these defenses.
Endpoint detection and response, or EDR, solutions provide a different capability to the security stack. With EDR in place, security teams can continuously collect, record, and store endpoint data, providing them with surveillance-like visibility they can use to investigate a past incident or to proactively hunt for threats in their environment.
EDR is often equated to highly skilled security professionals or security operations centers (SOCs), who use their advanced experience and knowledge to navigate the EDR data stores to uncover subtle activities that indicate compromise. However, next-generation antivirus (NGAV) solutions are now incorporating EDR capabilities to help security teams of all sizes and skill levels identify threats and investigate incidents beyond prevention.