PROFESSIONAL SERVICES
Where Protection Gets Personal
Every security situation is different. Let our experts help you identify blind spots, respond to incidents and find the most effective solution for your needs and budget.
As mission-critical networks evolve into dynamic systems of interconnected networks with more open-source platforms and cloud-based solutions, governance and oversight throughout the system’s operational lifecycle are required. This encompasses a coordinated and regular re-evaluation of people, processes, and technology to assure organizational readiness to protect, detect and respond to evolving threats
Our experienced professional services consultant and engineers listen and understand your cybersecurity needs and goals, then put together a solution that is right and unique for you.
We use industry best practices blended with real-world experiences to ensure customers attain business agility and maintain security control while enhancing customer experiences.
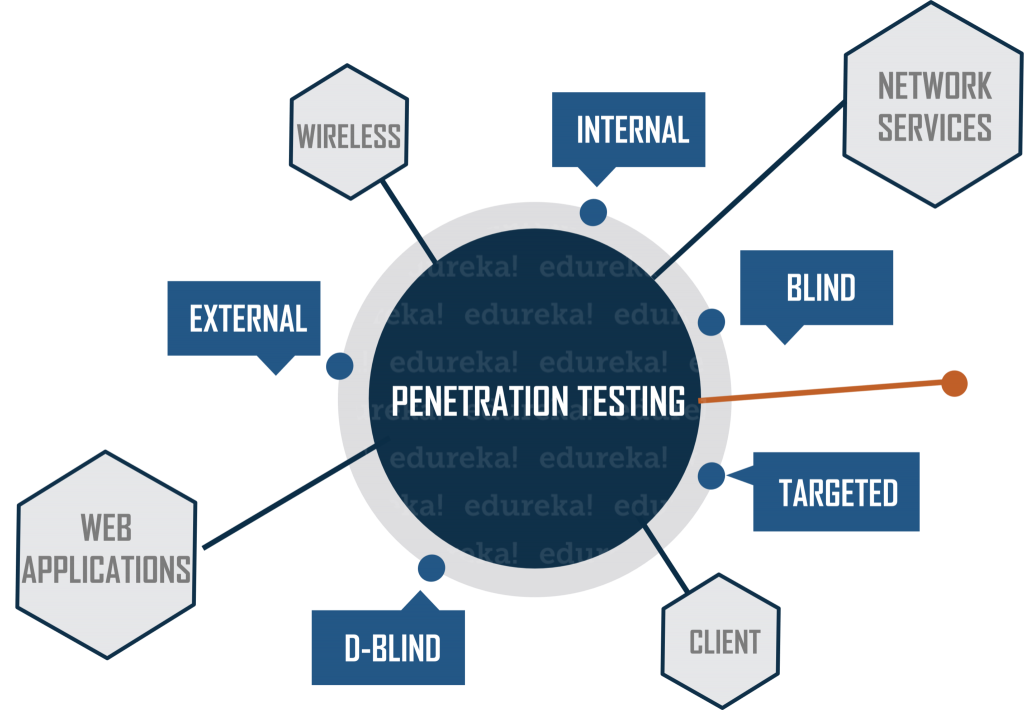
Penetration Testing
We use a controlled approach to penetration testing to fully assess the effectiveness of your organization’s control. We offer a variety of penetration testing options that assess different aspects of your organization’s security environment
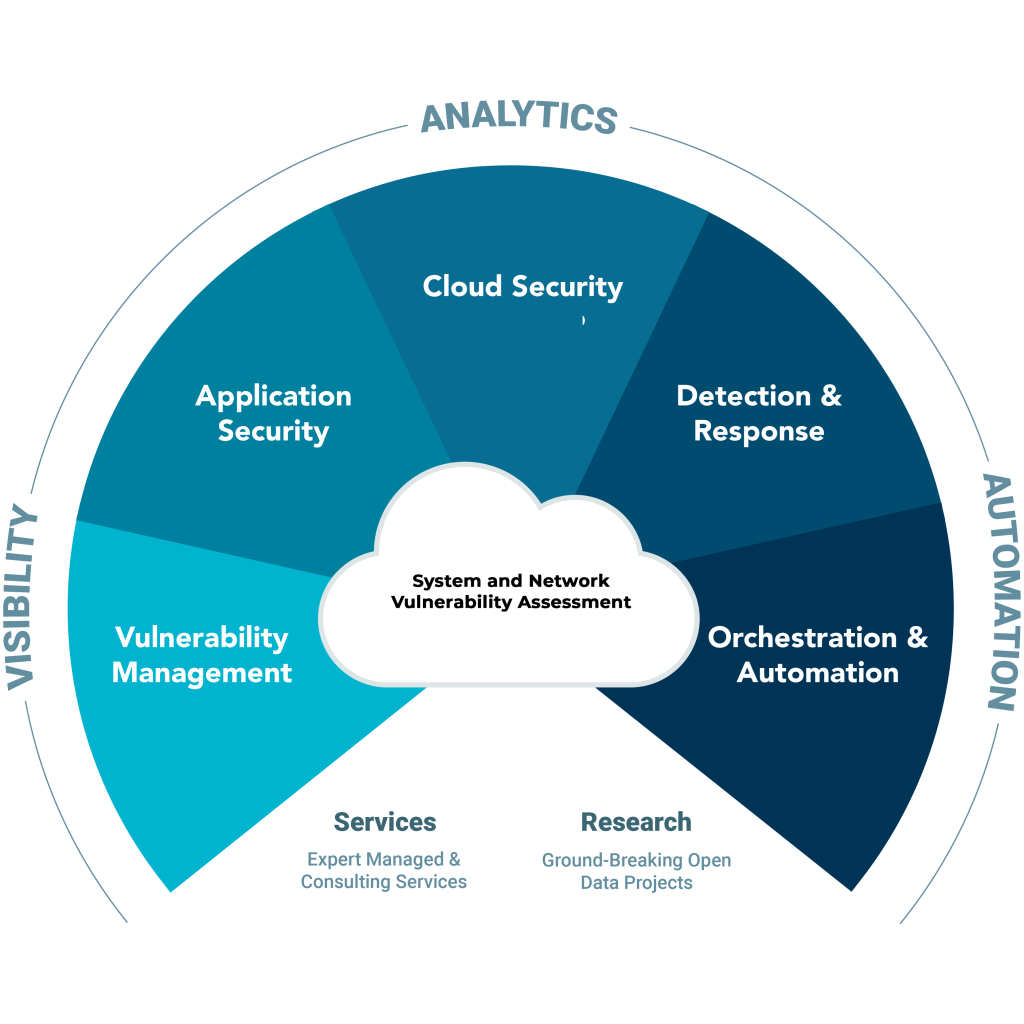
System and Network Vulnerability Assessment
Our comprehensive security services examine your applications and entire network for common input validation vulnerabilities to language, coding or platform-specific weakness.
Compromised Assessment
Would you know if you had been attacked or if your organization’s information and infrastructure security were at risk?
We combine our advanced knowledge of breaching environments with new breach detection technology to determine if attackers are currently in your environment or have been active in the past
Our compromised assessment service will:
- Identify the presence of any ongoing breaches
- Illustrate gaps in your existing visibility
- Provide insight into whether you have suffered a breach
Develop a remediation plan to address your security needs
Risk Assessment
Risk management is often treated as a compliance issue. However, truly understanding the risks to strategic initiatives and information security requires a different approach.

