NEXT GENERATION SIEM
Legacy, signature-based SIEMs aren’t effective at detecting advanced threats.
The only way to catch a sophisticated attacker in time is to leverage advanced analytics within your SIEM. Stay ahead of the attackers by using technology such as machine learning to give your security team better insights and less false positives.
Solve Security Challenges With Next-Generation SIEM
Advance On-Boarding: Environment Hardening and CIS Top20 Controls
24x7x365 SOC services based on NIST-800 Framework
Best of Breed security applications and technology stack.
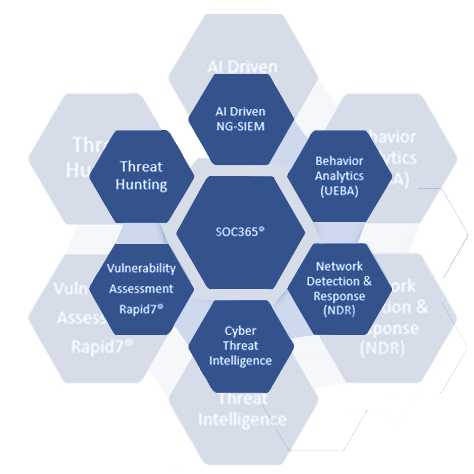
The World’s First Converged XDR Security Platform.
Unified visibility of cloud and On-prem assets
Vulnerability Scanning & Reporting
State of the Art Technology Stack
Regulatory Compliance
Specialist SOC Team
Faster Time to Security Value
Automatically Parse Logs
Each system you monitor uses different data formats – for any SIEM to effectively link log records, it must first parse (extract relevant data) from raw logs. Typical SIEMs require a lot of work from your team to develop and maintain parsers.
SOC365 XDR platform does that work for you, making it easy and simple to set up the cloud-delivered solution in your environment and automatically start seeing security value.
Context-Rich Data
Automatically Parse Logs
Each system you monitor uses different data formats – for any SIEM to effectively link log records, it must first parse (extract relevant data) from raw logs. Typical SIEMs require a lot of work from your team to develop and maintain parsers.
SOC365 XDR platform does that work for you, making it easy and simple to set up the cloud-delivered solution in your environment and automatically start seeing security value.
Correlated Security Data
Automated Threat Analysis
SOC365 platform integrates with multiple threat intelligence feeds to match events with the most up-to-date threat information, automatically correlating threats with data, doing the analysis for you. We detect incidents related to ransomware, data exfiltration, lateral movement and more.
No need to comb through large volumes of datasets manually for investigation and response. Our security analysts do even more work for you; writing detection rules for threat hunting to reduce the time your team needs to spend on tracking down security incidents
Built-in Threat Analysis
Detect, Investigate & Analyze
Don’t have time or the team to investigate every alert? Commtel security team works behind the scenes, proactively hunting threats and providing you with automated analyses and advice on next steps. Our Threat Feed allows you to compare incoming network traffic against multiple threat intelligence feeds to inform you of malicious activity in realtime. Still have questions? We’re available to answer them, as your trusted security advisor
World-class Vulnerability Management
Collect, Prioritize & Remediate
Vulnerabilities pop up every day. You need constant intelligence to discover them, locate them, prioritize them for your business, and confirm your exposure has been reduced. Nexpose, Rapid7’s on-premises vulnerability management software, monitors exposures in real-time and adapts to new threats with fresh data, ensuring you can always act at the moment of impact.
Our security experts perform vulnerability scanning on weekly basis on your critical assets and report the findings with remediation guidelines.

